San Francisco Transit Hacker Hacked
Ashley Allen / 7 years ago
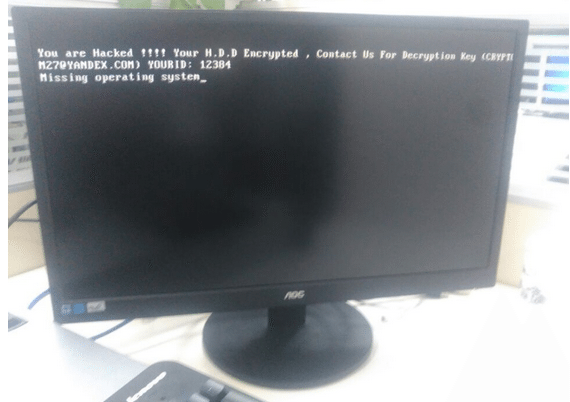
Over the weekend, it emerged that the San Francisco Municipal Rail system (SFMTA) had been hacked, with employees greeted by ransomware on their computer terminals. In a delicious twist, an interested party who read about the San Francisco transit ransomware – in an article which listed the attacker’s e-mail address – decided to hack the hacker back. KrebsOnSecurity was contacted yesterday by an anonymous security researcher who had compromised cryptom2016@yandex.com, which sent ransomware demands requesting 100 Bitcoins (approximately $73,000).
“On Monday, KrebsOnSecurity was contacted by a security researcher who said he hacked this very same cryptom27@yandex.com inbox after reading a news article about the SFMTA incident,” the report reads. “The researcher, who has asked to remain anonymous, said he compromised the extortionist’s inbox by guessing the answer to his secret question, which then allowed him to reset the attacker’s email password. A screen shot of the user profile page for cryptom27@yandex.com shows that it was tied to a backup email address, cryptom2016@yandex.com, which also was protected by the same secret question and answer.”
KrebsOnSecurity enlisted the help of a number of experts to interpret the data purloined from the malicious e-mail account and found that the hacker had been scanning the internet for vulnerabilities they could exploit.
“It appears our attacker has been using a number of tools which enabled the scanning of large portions of the Internet and several specific targets for vulnerabilities,” Alex Holden, chief information security officer at Hold Security Inc., said. “The most common vulnerability used ‘weblogic unserialize exploit’ and especially targeted Oracle Corp. server products, including Primavera project portfolio management software.”
SFMTA was able to restore its systems without ceding to the hacker’s demands, with KrebsOnSecurity applauding the organisation for keeping extensive data backups for its systems. The hackers use of security questions, meanwhile, has been used as an example of what not to do when securing your accounts.
“As the SFMTA’s experience illustrates, having proper and regular backups of your data can save you bundles. But unsecured backups can also be encrypted by ransomware, so it’s important to ensure that backups are not connected to the computers and networks they are backing up,” KrebsOnSecurity says. “Finally, as I hope this story shows, truthfully answering secret questions is a surefire way to get your online account hacked.”



















