Popcorn Time Vulnerability Leaves Users Open to Attack
Ashley Allen / 9 years ago

A security engineer has found a vulnerability in popular pirate movie application Popcorn Time that could leave users’ devices open to being hacked by a “man-in-the-middle” attacker. Antonios Chariton (aka ‘DaKnOb’), a Security Engineer & Researcher living in Greece, found the vulnerability in at least one fork of Popcorn Time’s code, and warn users that using the software in its present form could be a risky proposition.
“There are two reasons that made me look into Popcorn Time,” Charlton said. “First of all, I know many people who have installed this application on their personal computers and use it, and second of all, by pure accident: I was setting up my computer firewall when I noticed the network traffic initiated by Popcorn Time.”
Popcorn Time uses Cloudflare to bypass ISP-level blocking in the UK – “a really smart” technique, according to Charlton – but the lack of layered security on top of that system is what leaves Popcorn Time open to attack.
“First of all, the request to Cloudflare is initiated over plain HTTP. That means both the request and the response can be changed by someone with a Man In The Middle position (Local Attacker, Network Administrator, ISP, Government, etc.),” Chariton explained. “The second mistake is that there is no input sanitization whatsoever. That means, there are no checks in place to ensure the validity of the data received. The third mistake is that they make the previous two mistakes in a NodeJS application.”
Charlton exploited this vulnerability as a proof-of-concept, performing a “content spoofing” attack which changed the name of movie Hot Pursuit to Hello World:
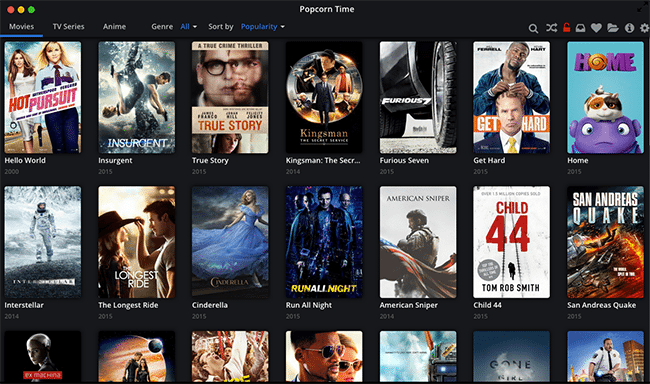
Using the same technique, Charlton could change any other information in Popcorn Time, but chose a method by which he could demonstrate the trick easily.
Next, he launched an XSS attack:
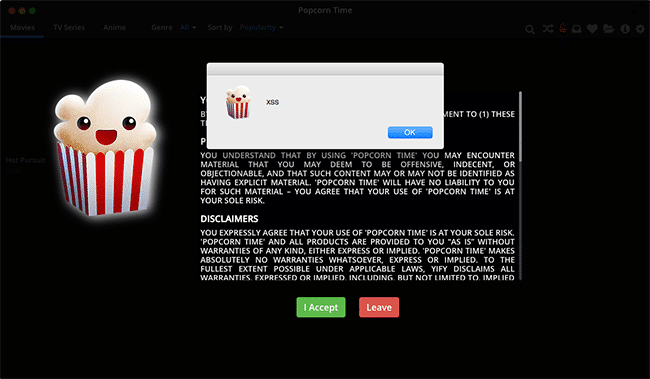
“We have injected malicious JavaScript and the client application executed the code. Using this attack we can show fake messages or even do something smarter. Since the application is written in NodeJS, if you find an XSS vulnerability, you are able to control the entire application,” Chariton said. “This essentially is Remote Code Execution on the computer that runs Popcorn Time. You can do anything the computer user could do.”
So, what can be done to protect users? Nothing on the user-end, sadly, but Charlton has some advice for Popcorn Time’s developers. “HTTP is insecure,” he warned. “There’s nothing you can do to change this. Please, use HTTPS everywhere, especially in applications that don’t run inside a web browser. Second, sanitize your input. Even if you receive something over TLS v1.2 using a Client Certificate, it still isn’t secure! Always perform client-side checks of the server response.”
“Last but not least, just because something is Open Source doesn’t mean it’s audited and secure. Discovering and exploiting this vulnerability was literally one hour of work, including the time to write all the JavaScript payloads and come up with cool stuff to do,” Charton adds.
Popcorn Time has responded to the threat, saying:
“This attack requires that the attacker is either inside the local network, inside the host machine, or has poisoned the DNS servers.
In any case, there are far more valuable attacks than simply hitting Popcorn Time. Especially because it does not run with elevated privileges and won’t let the attacker install new programs for example.”
Popcorn Time’s full statement can be found here.
Thank you TorrentFreak for providing us with this information.
Image courtesy of GeekZine.



















