Experts Find ‘Backdoor’ in iOS Functions that Allows Personal Data Monitoring
Gabriel Roşu / 10 years ago
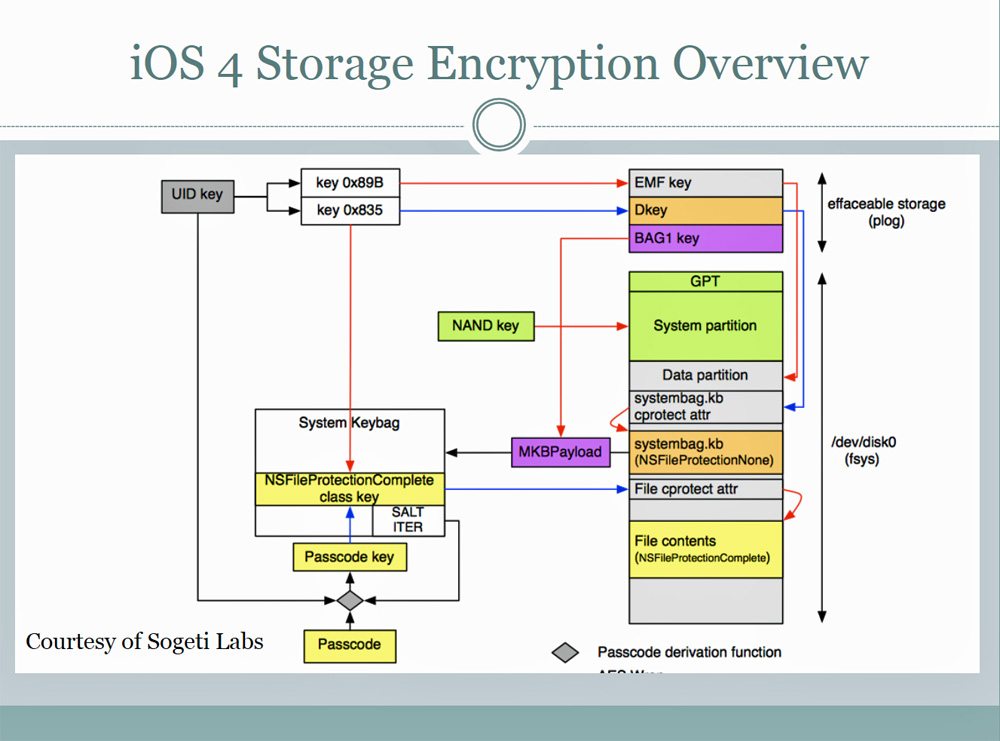
A forensic scientists warned people about the fact that Apple has undocumented functions in its iOS operating system which allows people to wirelessly connect and extract pictures, text messages and other sensitive data, without the need of either a password or PIN.
iOS jailbreaker and forensic expert, Jonathan Zdziarski, has apparently revealed the functions at the Hope X conference, where he stated that any device that has ever been paired with the target handset can be used to access the functions. Zdziarski has also stated that he is unsure of Apple engineers enabled the mechanism intentionally in order to make room for easier surveillance by the NSA or law enforcement groups.
The most concerning service of all is the com.apple.mobile.file_relay. It is said to generate a huge amount of data, including account data for email services, Twitter, iClound, a full copy of the address book including deleted entries, the user cache folder, geographic position logs, a complete dump of the user photo album, and many more. All the data is available and accessible without requiring any additional security protocols, such as passwords or PINs.
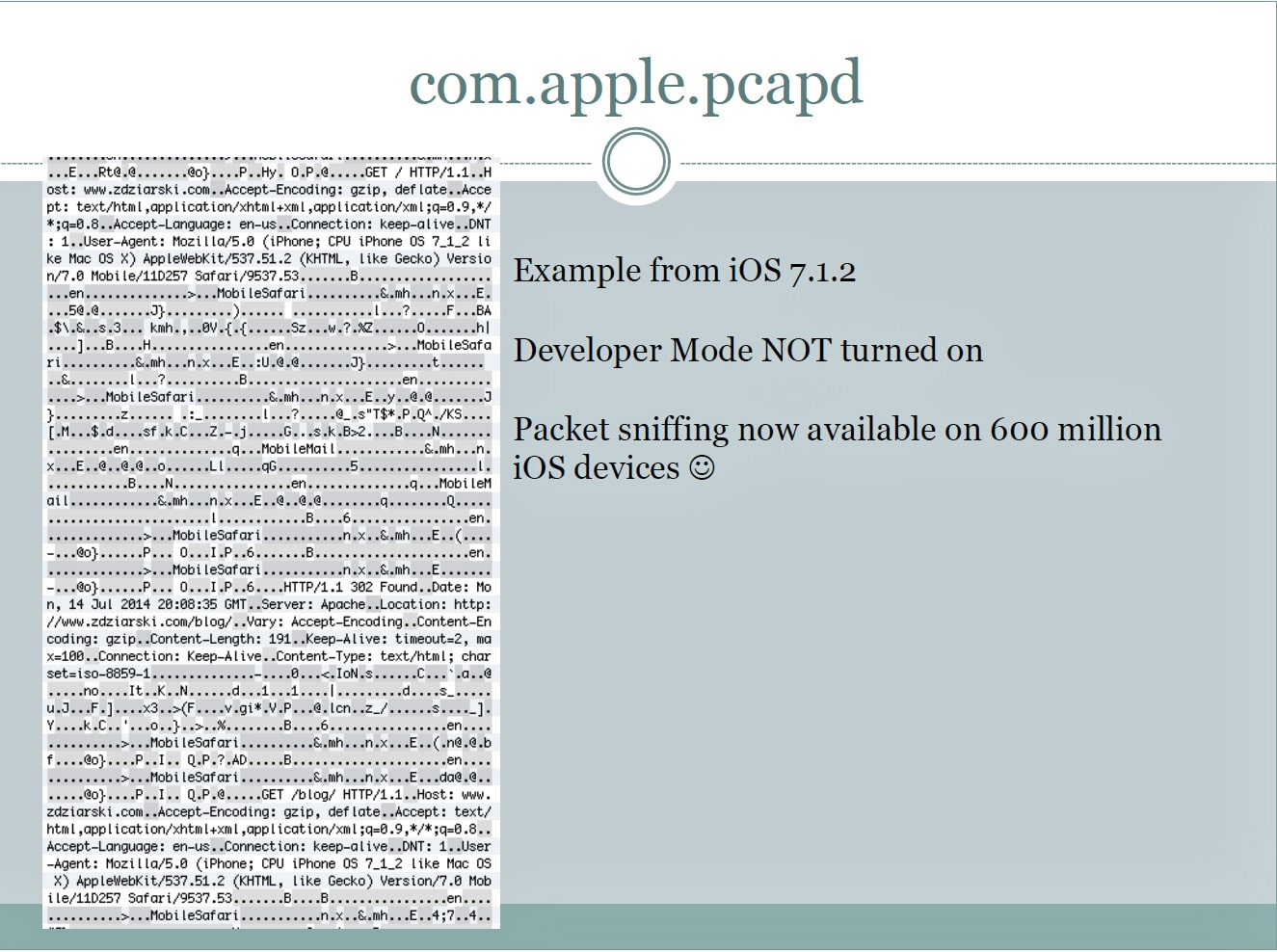
Zdziarski has also added two other services, the com.apple.pcapd and com.apple.mobile.house_arrest, stating that the latter may have legitimate uses for app developers or support engineers. However, the data generated can be used to spy on users by government agencies or anyone who knows how to access the logs. For example, the pcapd allows people to wirelessly monitor all network traffic traveling into and out of the device, even when the handset is not running in a special developer or support mode. In addition, the house_arrest allows the copying of sensitive files and documents from Twitter, Facebook, and many other applications.
While the services are available and can be read by all, Zdziarski tells that not every hacker out there is out to get your data. He said that only “technically knowledgeable people who have access to a computer, electric charger, or other device that has ever been modified to digitally pair with a targeted iPhone or iPad” can access the data.
Thank you Arstechnica for providing us with this information
Images courtesy of Arstechnica



















