Intel SGX Breached by New Speculative Execution Exploit
Samuel Wan / 6 years ago
Foreshadow Hits Secure SGX Secure Enclaves
With the release of Spectre and Meltdown, the floodgates have opened. Since the reveal of the two speculative exploits last year, more bugs have come out of the woodwork. One recent release was a variant of Spectre targettable over networks. Today, we have a new bug that hits Intel right in the jaw. Dubbed Foreshadow by researchers, the new exploit targets the supposedly secure SGX function on Intel CPUs.
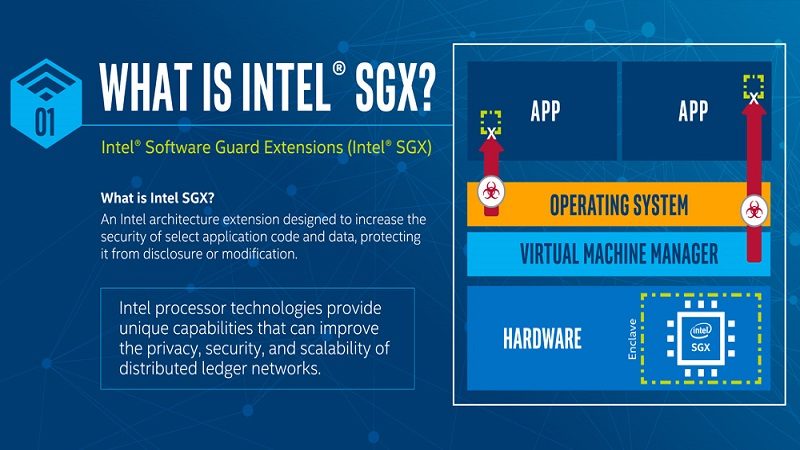
SGX or Software Guard eXtensions is a new feature Intel introduced with Skylake and Kaby Lake. SGX allows the creation of Trusted Execution Environments or TEEs. These TTEs are created using SGX to create a secure enclave. Due to this secure enclave, blocks of memory or code is supposed to be protected from everything. Furthermore, this includes protection from a hostile kernel, hypervisor or operating system. Foreshadow circumvents this and ploughs right on through into the secure enclave. This feature is great for cloud virtual machines because it protects against hostile hosts and neighbours.
Intel Microcode Fix Mostly Patches the Exploit
Foreshadow works in a similar fashion to Meltdown. In fact, it builds on the speculative nature of the original attack. Normally, SGX protects the enclave data with encryption. However, the CPU decrypts protected data in the L1 cache. Once there, Intel CPUs do not perform any further protection checks. This allows the attacker to exploit the speculative execution behaviour of the CPU, like in Meltdown to read the data. The attacker can also create malicious enclaves to more easily attack other enclaves on the same core. This only works on CPUs with Hyper-Threading since they share the same logical core. All said and done though, SGX still makes the attacker’s job more difficult as Intel wants it to do.
Luckily for users, Intel has already rolled out a fix. Updated microcode has been provided to change CPU SGX function. After using the data, the CPU will flush the L1 Data cache immediately. Unfortunately, this does not fully fix the flaw with Hyper-Threading. This is because the 2 enclaves on each virtual core share the L1. This is problematic for cloud servers which now have to worry about shared Hyper-Threaded cores. Finally, Intel plans to provide a hardware fix to this issue in Cascade Lake. Given the state of things though, only more attacks are likely to come out in the meanwhile.