No Need to Shoot Down Nuisance Drones – Hack Them Instead
Ashley Allen / 8 years ago
The proliferation of consumer drones in the last decade has been a boon for remote-control flying enthusiasts and filmmakers, but not so much for public servants – like police and fire services – not to mention normal people, either concerned for their privacy or just annoyed over the flying devices invading their personal space. In the US, at least, an increasingly common response to nuisance drones is to shoot them out of the sky. New work, undertaken by researchers, though, reveals that there may be a more effective (and more insidious) method of dealing with problem drones: hacking them.
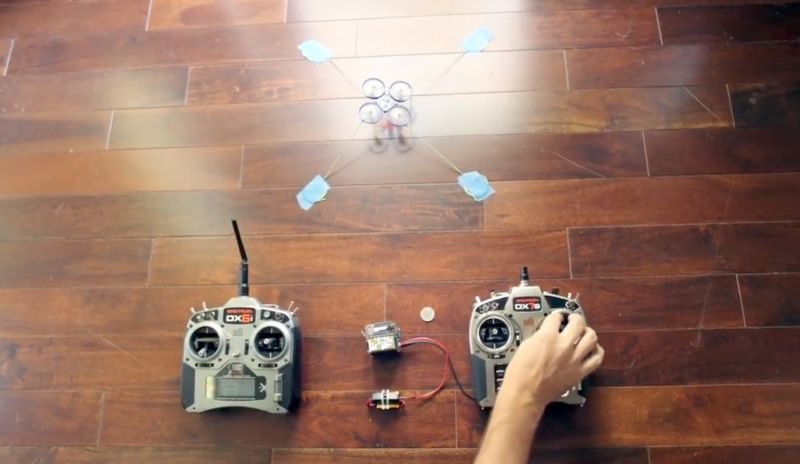
Developed by PacSec Security, the drone hijacker is a radio transmitter that can seize control of any operational drone, even in mid-flight. Once the hijacking device takes control of a drone, the original operator loses all control over it. The hijacking device, which is capable of controlling any drone that communicates over DSMx, was presented by researcher Jonathan Andersson at the PacSec hacking conference in Japan on Wednesday (26th October).
“It’s not a jamming system so I am not competing for control via RF power,” Andersson told Vulture South (via The Register). “Full flight control is achieved with the target experiencing a complete loss of control — it’s a clean switch-over. The range of my proof of concept implementation is equal to a standard DSMx radio transmitter, though standard 2.4GHz ISM band amplification can be applied to extend the range.”
“In the defense and security world, there are people who have done this,” Robi Sen, the founder of counter-drone product maker Department 13, told Ars Technica. “There are also a few hackers who have done this but have not made their research public. To my knowledge, this is the first time that this has all been presented, in a complete package, publicly.”
In addition to drones, vulnerable DSMx-based systems include RC aeroplanes, cars, and boats. While the vulnerability could be remedied by updating the firmware of DSMx receivers, the majority of devices are unable to be accessed in such a manner by users since they are lacking in Wi-Fi or other internet and data transfer connectivity.
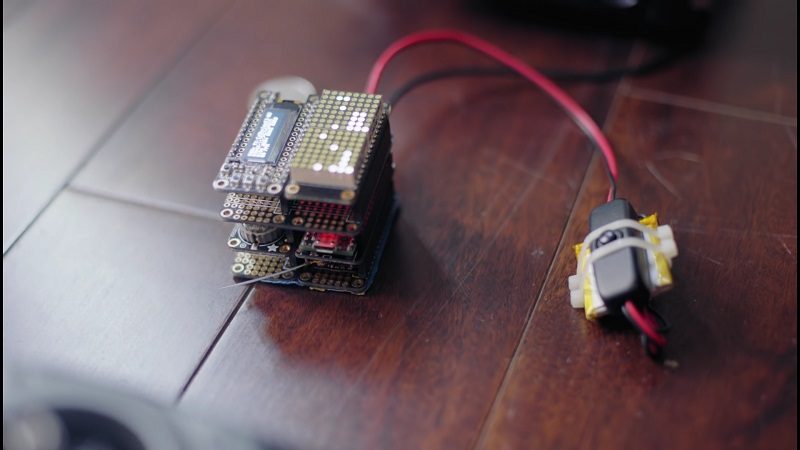
“The shared secret (‘secret’ used loosely as it is not encrypted) exchanged is easily reconstructed long after the binding process is complete by observing the protocol and using a couple of brute-force techniques,” Andersson wrote in an e-mail to Ars Technica. “Further, there is a timing attack vulnerability wherein I synchronize to the target radio’s transmissions and transmit a malicious control packet ahead of the target, and the receiver accepts my control information and rejects the target’s.”
“My guess is that it will not be easy to completely remedy the situation,” Andersson added. “The manufacturers and partners in the ecosystem sell standalone radio transmitters, models of all kinds, [and] transmitters that come with models and standalone receivers. Only a certain set of standalone transmitters have a firmware upgrade capability, though the fix is needed on the model/receiver side.”



















